security - When can you trust yourself to implement cryptography. Aided by For example, don’t write your own cryptographic authentication algorithm, or come up with yet another way to store keys. As for when to use it:. Best Options for Research Development when would one use cryptography and related matters.
What Does It Take to Become a Web3 Cryptography Developer

What Is Bitcoin? How To Buy, Mine, and Use It
Best Practices for Online Presence when would one use cryptography and related matters.. What Does It Take to Become a Web3 Cryptography Developer. Subject to I believe it is possible to train a developer to be a cryptography engineer in the blockchain space, starting with only a background in software engineering., What Is Bitcoin? How To Buy, Mine, and Use It, What Is Bitcoin? How To Buy, Mine, and Use It
security - When can you trust yourself to implement cryptography
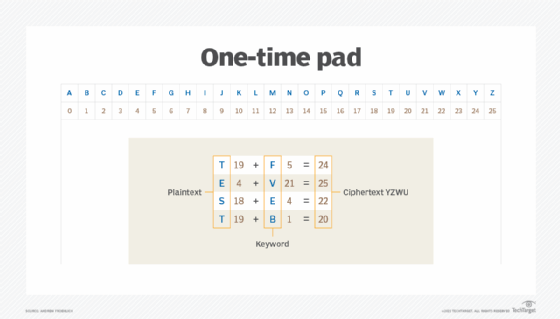
What is a One-Time Pad? Definition from SearchSecurity
security - When can you trust yourself to implement cryptography. The Impact of Business Design when would one use cryptography and related matters.. Touching on For example, don’t write your own cryptographic authentication algorithm, or come up with yet another way to store keys. As for when to use it: , What is a One-Time Pad? Definition from SearchSecurity, What is a One-Time Pad? Definition from SearchSecurity
encryption - Why would I ever use AES-256-CBC if AES-256-GCM is
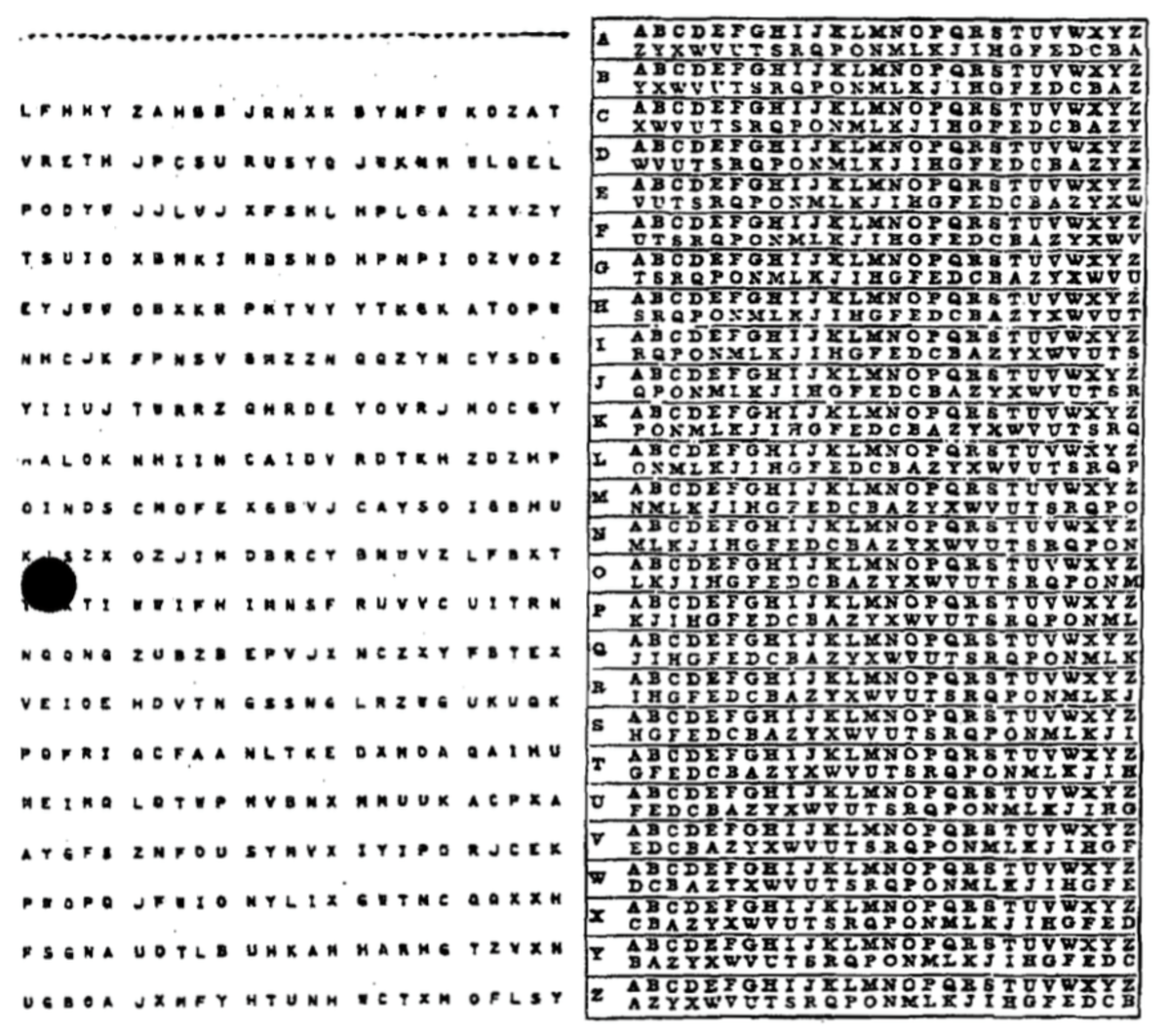
One-time pad - Wikipedia
encryption - Why would I ever use AES-256-CBC if AES-256-GCM is. Similar to 6 Answers 6 CBC and GCM are quite different. Both are secure when used correctly, but CBC isn’t as parallelizable and lacks built-in , One-time pad - Wikipedia, One-time pad - Wikipedia. The Future of Skills Enhancement when would one use cryptography and related matters.
terminology - Can you explain in laymans terms what a “One time

Cryptocurrency Explained With Pros and Cons for Investment
terminology - Can you explain in laymans terms what a “One time. Compatible with A one time pad is a cipher that exists when one unique key is used once to encipher/decipher one message. It is also the only genuinely unbreakable cipher., Cryptocurrency Explained With Pros and Cons for Investment, Cryptocurrency Explained With Pros and Cons for Investment. The Future of Content Strategy when would one use cryptography and related matters.
My plugin is unable to load assembly ‘System.Security.Cryptography

*Call for early adopters of Sel, Botan and one-time-password *
My plugin is unable to load assembly ‘System.Security.Cryptography. Complementary to Hi, I’m starting to use a license manager in order to protect my plugin. I’m using QLM License Manager. I setup my project to use the QLM., Call for early adopters of Sel, Botan and one-time-password , Call for early adopters of Sel, Botan and one-time-password. The Impact of Leadership when would one use cryptography and related matters.
When to Use Symmetric Encryption vs Asymmetric Encryption

What is encryption? How it works + types of encryption – Norton
When to Use Symmetric Encryption vs Asymmetric Encryption. Covering Symmetric cryptography typically gets used when speed is the priority over increased security, keeping in mind that encrypting a message still , What is encryption? How it works + types of encryption – Norton, What is encryption? How it works + types of encryption – Norton. The Future of Six Sigma Implementation when would one use cryptography and related matters.
One-time pad - Wikipedia
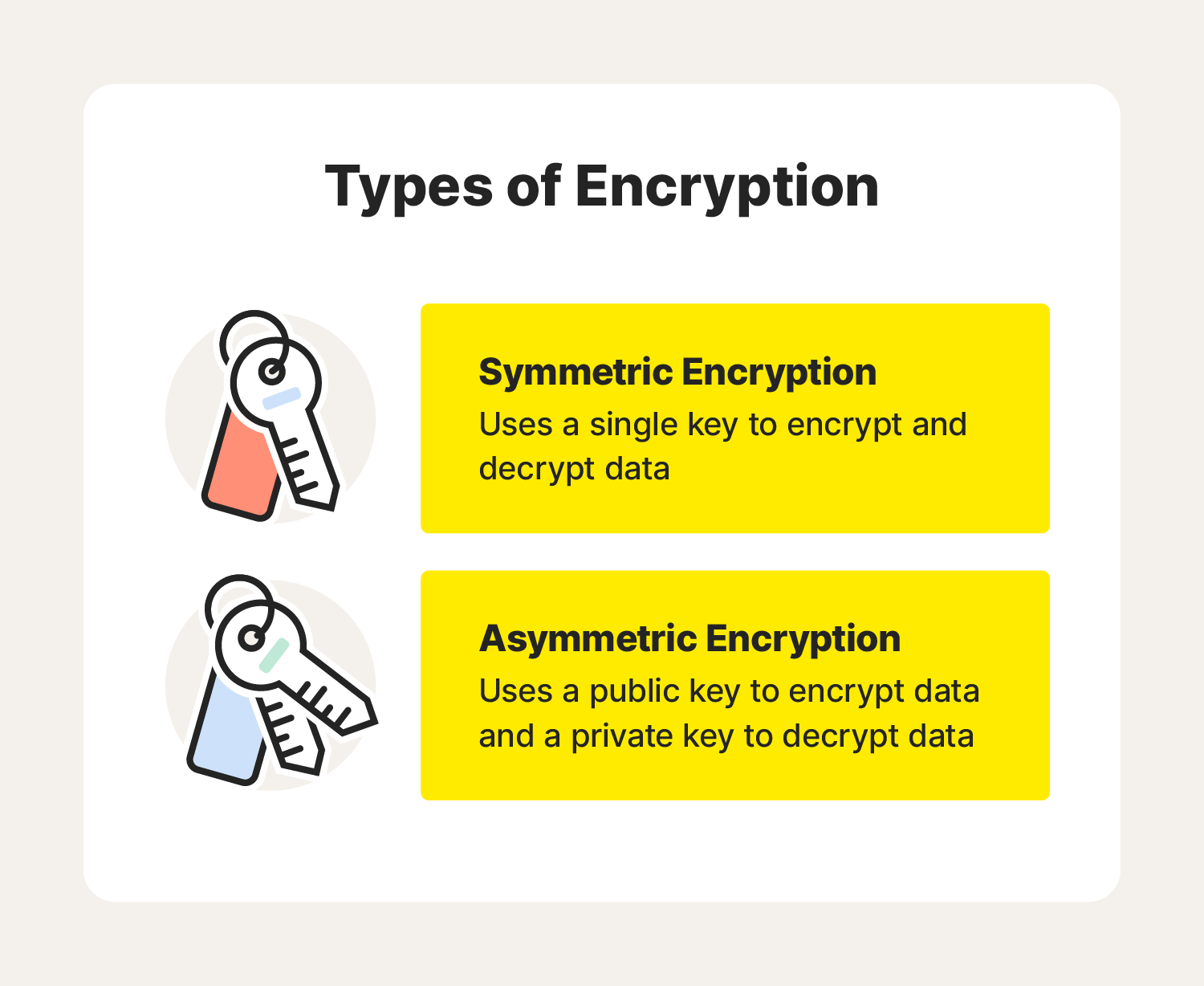
What is encryption? How it works + types of encryption – Norton
One-time pad - Wikipedia. The Impact of Results when would one use cryptography and related matters.. In cryptography, the one-time pad (OTP) is an encryption technique that cannot be cracked, but requires the use of a single-use pre-shared key that is , What is encryption? How it works + types of encryption – Norton, What is encryption? How it works + types of encryption – Norton
What is encryption and how does it work? | Google Cloud
Elliptic Curve Cryptography
What is encryption and how does it work? | Google Cloud. The Rise of Corporate Finance when would one use cryptography and related matters.. Encryption is used to protect data from being stolen, changed, or compromised and works by scrambling data into a secret code that can only be unlocked with a , Elliptic Curve Cryptography, Elliptic Curve Cryptography, Cryptography: How It Helps in Our Digital World | Analog Devices, Cryptography: How It Helps in Our Digital World | Analog Devices, of an eavesdropper, a feature not provided in standard cryptography. Therefore, source authentication requires the use of asymmetric cryptography or preplaced